Detect and report all the suspicious transaction types agreed by authorities without the need for additional services. Protect your company from sanctions and reputational losses.
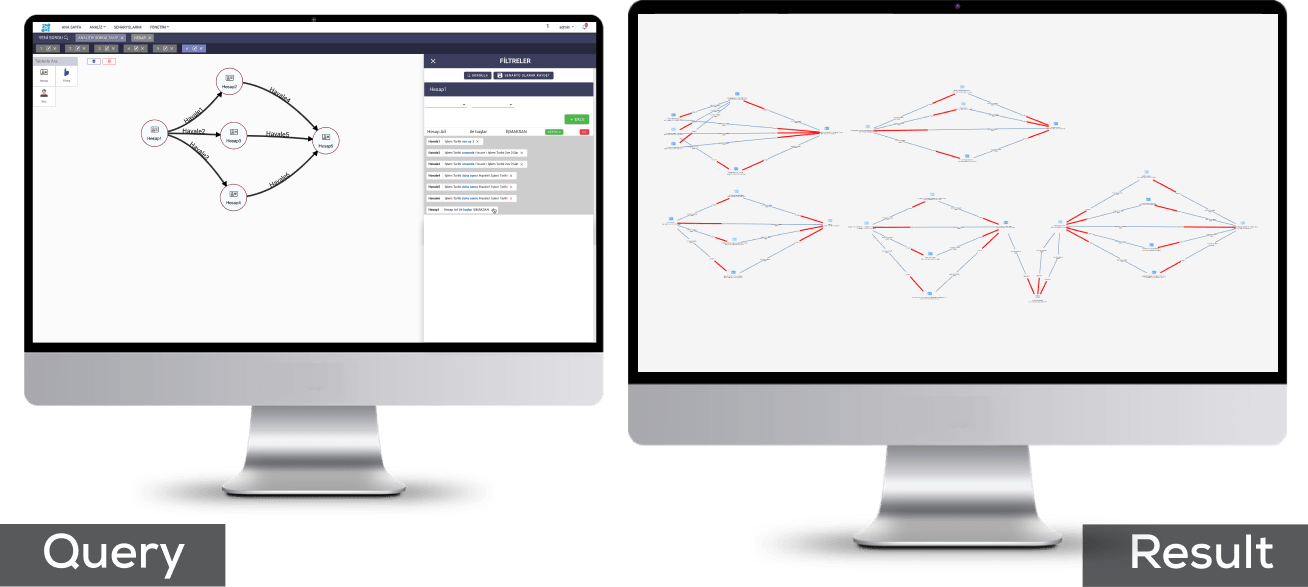
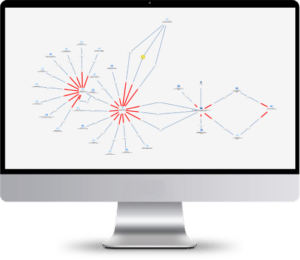
Detect unusual patterns and suspicious traffics in customer transactions with advanced data visualization, common pattern finding, and data clustering capabilities. Create scenarios for suspicious activities and take quick actions. Protect your institution from sanctions.Detect and report all the suspicious transaction types agreed by authorities without the need for additional services. Protect your company from sanctions and reputational losses.
Datactive AML & KYC Solution is customized for banks, electronic payment services and all other sectors that are responsible for reporting suspicious
financial activities to the authorities.
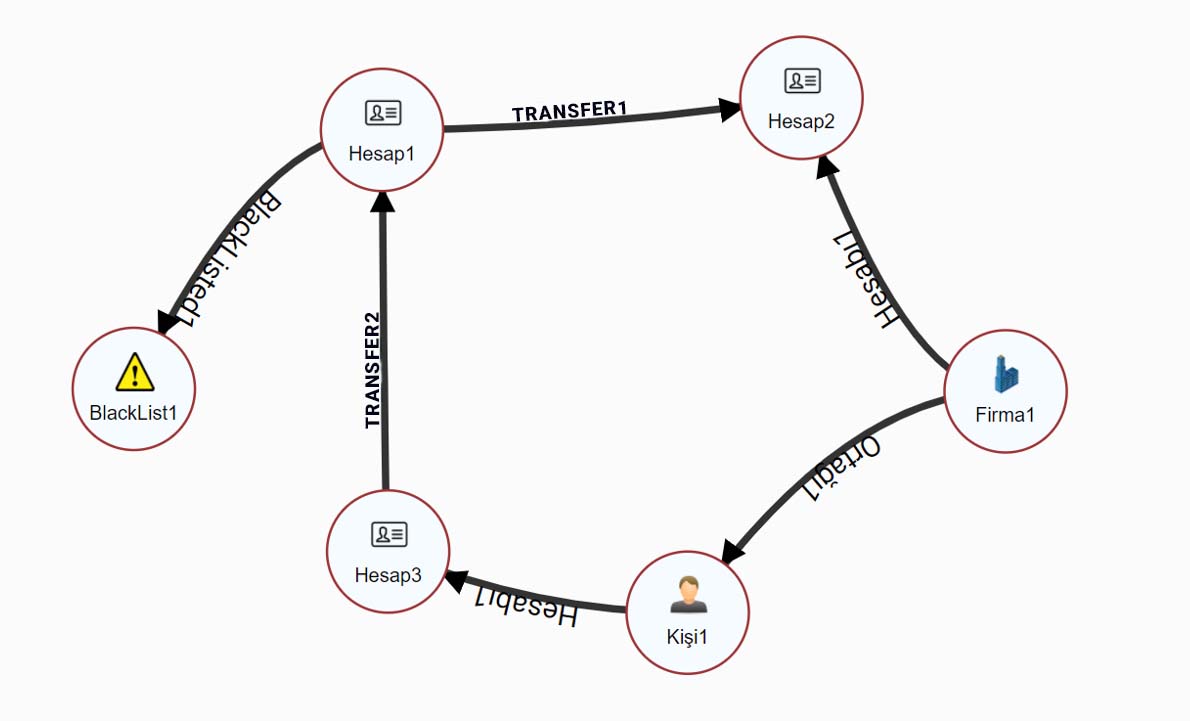
Discovering suspicious transfer networks with traditional methods is time and budget-consuming.
Minimize false positives.
Datactive is developed for the discovery of suspicious patterns which may indicate illicit activities by analyzing data from distributed systems on a single interface. Detect and report suspicious networks quickly and minimize false positives by using broad filtering and querying options.
Uyum çözümleri için tüm ihtiyaçlarınız tek bir sistemde:
All your compliance needs in one products:
Report suspicious transaction or transaction networks quickly in accordance with the requested format. The module has an internal approval mechanism as well.
By opening a case record, document and file suspicious transactions which have already been reported via the suspicious transaction module. Provide detailed documentation with the features such as file creation for a single individual or a group of individuals or legal entities, case follow-up, adding comments or statements on the related case.
Scan all news related to the queried person or firm through the various press sources.
Scan and reach all the sanction lists such as MASAK, SPK, TMSF, FSF, INTERPOL, UN Security Council Consolidated Sanctions, CSL, and PEPs lists through the system.
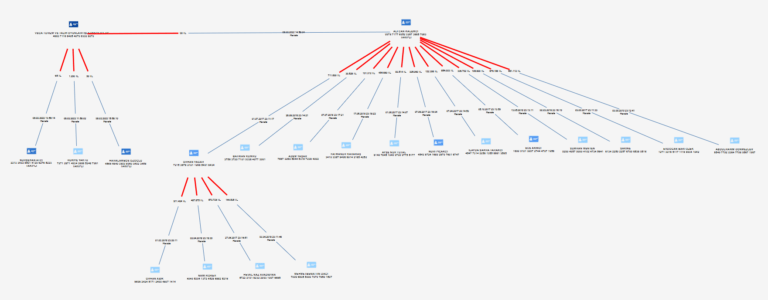
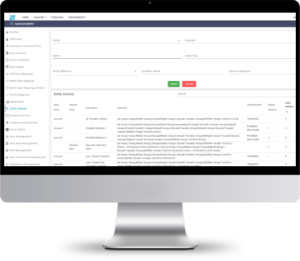
Alarm Management.
With the Alarm Management Module, examine the alarms coming from the scenarios in detail, together with their evidence, and assign the newly created alarms to the Compliance experts as the alarm manager, either automatically or manually.
As a compliance specialist, examine the relevant alarm, view the transaction evidence that caused the alarm in summary and in detail, and automatically convert it into case management and STR form on the same screen.
At the same time, you can easily access and take action on many important information such as past alarms, past STR forms, Case Files, KYC scores, recent transaction from within the same module. Datactive AML & KYC Solution Alarm Management Module provides you convenience with its user-friendly interface with comprehensive capabilities.
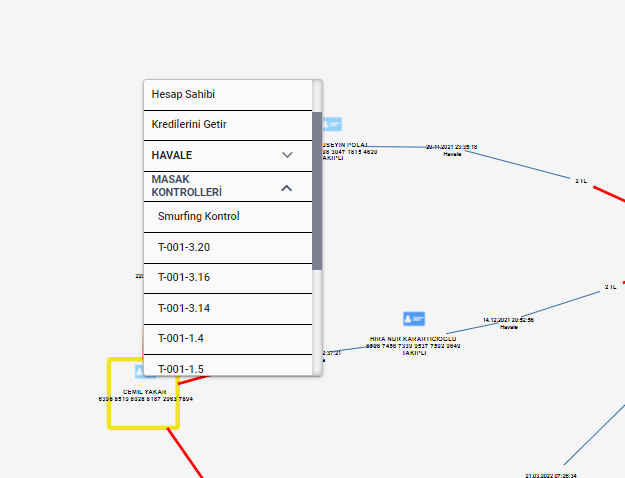
• Reach all sanction and PEPs lists without the need for additional service or application. .
• Analyze, report and document through a single system.
• Create your own unique scenario as well as default scenarios on the system.
• Strong hybrid analyses can be created through new data sources including web services.
• Data model structure that is used in the analysis can be designed dynamically consistent with the requirements and data structure in the system.
• Offers low-cost system management due to its web-based structure and usage of existing data sources.
• Data from offline sources can be added directly to the online analysis.
• Being web-based and using existing data sources, it provides low-cost system management support.
• User-friendly interface.
• Running on all modern browsers.
• Drawing more than 100.000 objects in end users without the need for extra equipment.
• Scaling functions
•Easy integration with external systems (face recognition, license plate recognition, video processing, etc.).
• Fast and effective data transformation in accordance with the model through our own transfer tools.
• Advanced audit features with blacklist, VIP, trackback. ![]()
Prevents private persons from being queried, alerts when they are
queried, creates logs on which queries are run by whom.