Financial crime intelligence systems differ from rule-based transaction monitoring systems, which monitor the transaction and cancel the transaction if fraud is suspected. In this article, we will examine the differences between them.
Almost all banks use rule-based transaction monitoring systems for fraud detection. These systems create a customer profile by using past transactions, transaction locations, transaction type, and daily average transaction amount or frequency information. When there is an unusual transaction that conflicts with the user profile, the system stops the transaction and informs the customer. These systems, which are based on the monitoring of individual transactions, are crucial for the protection of individuals. However, detected fraudsters may often be a part of larger crime networks. To solve the crux of the problem, it is necessary to detect criminal organizations. Financial institutions have to adopt stricter rules against organized financial crime and money laundering methods. Detection of financial crimes should not only be seen as an obligation to inform The Financial Crimes Investigation Board, activities such as money laundering also have great negative social impacts. This type of organized crime can finance activities such as terrorism and drug trafficking. Therefore, financial institutions are obliged to detect organized networks in order not to be an indirect intermediary and to protect their reputation and customer loyalty.
At this point, criminal intelligence software comes into play. Financial crime intelligence software does not focus on instant transactions, instead, focuses on the detection of medium and large-scale crimes spread over time. These systems analyze, detect and visualize complex data patterns that indicate the possibility of illegal activity and reveal the connections between the data in a very short time.
Positioned as a crime intelligence software, Datactive enables the rapid extraction of new insights from large and complex databases to support the detection of unusual interactions and connections.
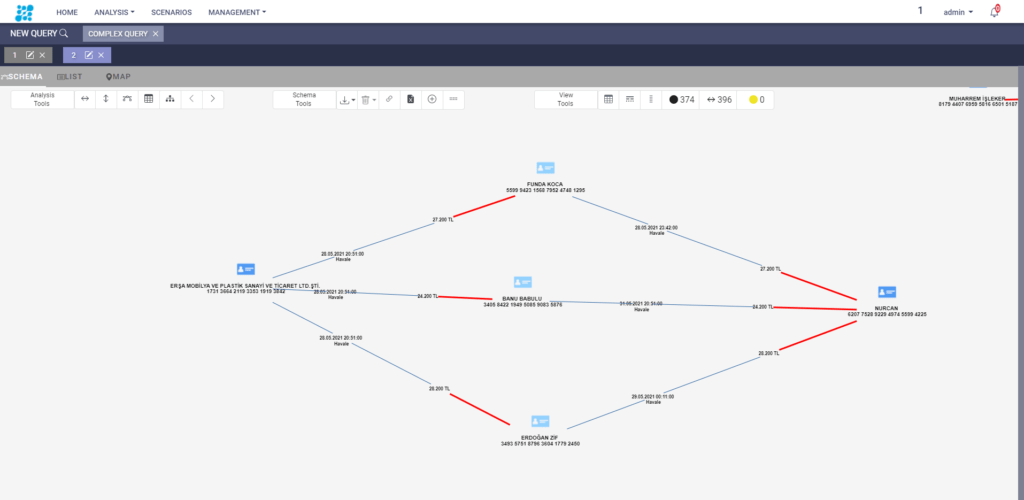
To uncover complex criminal networks, it is necessary to accurately identify suspicious patterns in general. With Datactive, a pattern is uncovered, tracked, another clue is captured, and anomalies are detected. Rule-based transaction monitoring systems are not developed for the detection of connections, wide-ranging relationships of individuals, and suspicious patterns. Planned crime networks have already discovered new ways to avoid being caught by transaction monitoring systems. Transactions carried out over time and with inconspicuous amounts may not be detected by the system. If such organized crimes are not detected, their financial and reputation damages to financial institutions in the medium and long term are much higher. This is where Datactive differs from rule-based transaction monitoring software. Regardless of the scope, crime networks are interconnected at some point. In this case, it is very important to be able to see the data in distributed systems on a single interface in a relationship-oriented way for the detection of these connections. This ability differs criminal intelligence systems from the transaction monitoring system.
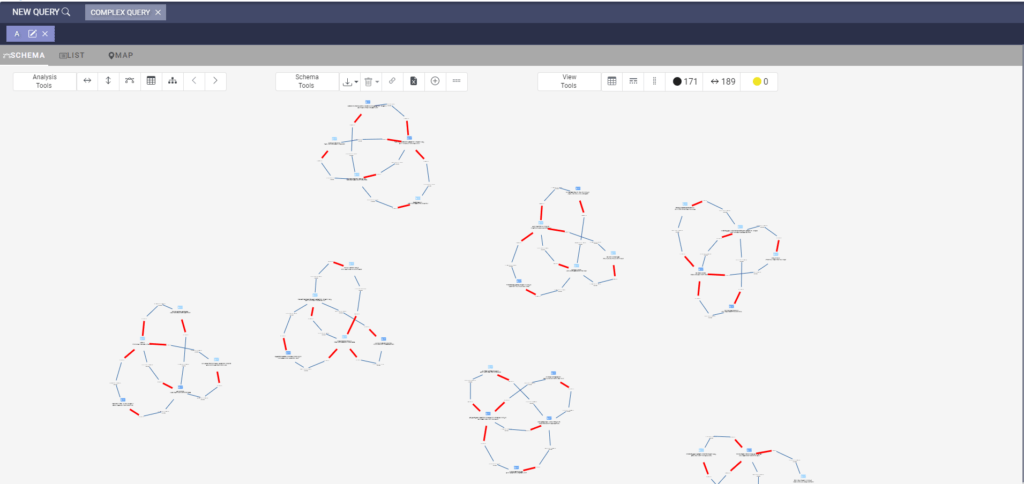
Although crime rings discover new methods, complex networks and their members always leave their digital footprints, and if these footprints are discovered, they can be easily traced. Datactive visualizes the connections between customer transactions, past transactions, individual relationships, etc. on a single interface. The scenario created for the suspected situation can be saved, an instant notification is received when there is a match, the status of the scenario can be tracked and the relevancy of the scenario can be measured. Moreover, increases in the number of suspicious patterns warn financial institutions of new crime methods.
Let’s demonstrate it through a use case: money laundering or fraud activities through online gambling or betting are common. In such cases, generally small and equal amounts are transferred from different persons to a single person or institution. However, the collected amount is then usually transferred to a specific person. This indicates that the winner of the game is already determined and money laundering may be carried out through these persons or institutions. It is difficult to uncover this case by using rule-based transaction monitoring systems. But when we create this scenario in Datactive, we instantly reveal compatible patterns and get detailed information about the people in this network. We can monitor suspicious activity by receiving alerts when there is any pattern that matches the case. Therefore, we detect a criminal network and discover their method by using Datactive, a financial crime intelligence system.
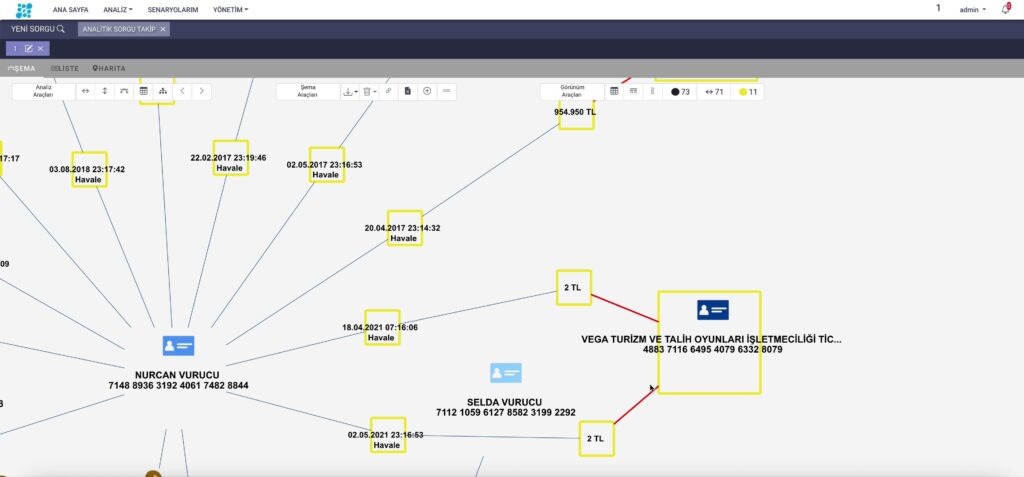
Datactive can be used by inspectors and internal audit specialists as well as compliance units to detect both internal and external frauds. A user-friendly interface provides non-IT units to conduct their investigations easily.
In summary, Datactive is not a rule-based transaction monitoring system that investigates a single transaction and intervenes it in case of suspicious activity. It is a financial crime detection analytics that enables the detection of more comprehensive criminal networks and organizations. The use of these systems is becoming widespread in our country as well. Financial institutions need a comprehensive analytical platform to fulfill their responsibilities for suspicious transaction reporting and to prevent illegal activities with a social dimension.
